
Cybercriminals are now after resumes. (Image generated by AI).
ResumeLooters – a new job scams threat
- Job scams have become a constant problem for those looking for jobs.
- ResumeLooters have stolen databases from job portals.
- ResumeLooters seem to be a new threat group as they only started operations around a year ago.
Job scams have been a constant problem for those looking for jobs. Many have fallen victim to fake job offers, with some even losing money or ending up in forced labor. In Southeast Asia, job scams have been such a huge problem that they involve human trafficking. Law enforcement agencies continue to clamp down on such activities in the region.
While these are physical job scams, virtual job scams have also become rampant. While some job portals have improved the types of jobs they advertise, many job sites still contain fake job advertisements. Social media companies are also trying to detect such scams, as platforms like LinkedIn have found themselves having to deal with these #FakeJobs.
Just as many thought the situation couldn’t get any worse, Group-IB has identified a large-scale malicious campaign primarily targeting job search and retail websites in the Asia-Pacific region.
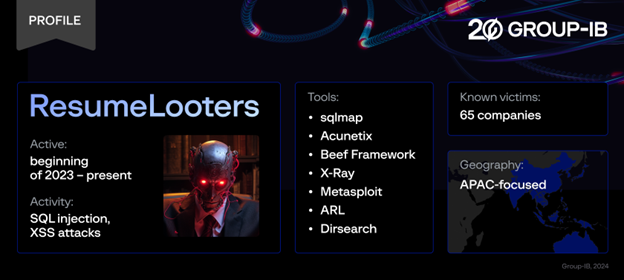
The group, dubbed ResumeLooters by Group-IB’s Threat Intelligence unit, successfully infected at least 65 websites between November and December 2023 through SQL injection and cross-site scripting (XSS) attacks. Most of the gang’s victims were in India, Taiwan, Thailand, Vietnam, China, and Australia.
Aside from the potential exposure of personal data, various APT groups could use the information for further targeting of specific individuals. For example, the Lazarus group had its infamous Dreamjob operation. The operation targeted hundreds of job seekers worldwide with job scams through fake job offers while it stole personal information and login credentials.
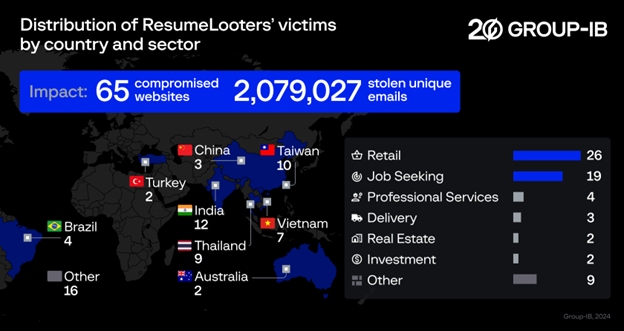
Most of the gang’s victims were found to be located in India, Taiwan, Thailand, Vietnam, China, and Australia. (Source – Group-IB).
ResumeLooters are worse than job scams
According to the report, ResumeLooters have stolen databases that contain 2,079,027 unique emails and other records, such as names, phone numbers, dates of birth, as well as information about job seekers’ experience and employment history. The stolen data was then offered for sale by ResumeLooters in Telegram channels. Group-IB has since issued notifications to the identified victims so they could take necessary measures to mitigate further damage.
ResumeLooters seem to be a new threat group as they only started operations around a year ago. The cyberthreat group has been utilizing several penetration testing frameworks and open-source tools, such as sqlmap, Acunetix, Beef Framework, X-Ray, Metasploit, ARL, and Dirsearch. This allowed the cybercriminal gang to inject malicious SQL queries into 65 job search, retail and other websites and retrieve a total of 2,188,444 rows, of which 510,259 were user data from employment websites.
Interestingly, most of the victims targeted by ResumeLooters are in the Asia Pacific region. This includes India, Taiwan, Thailand, Vietnam, China, Australia, the Philippines, South Korea and Japan. Victims outside of the region include Brazil, the US, Turkey, Russia, Mexico and Italy.
Group-IB also reported that two Telegram accounts were discovered to be associated with the threat actor. Both accounts have been used to offer the stolen data for sale in Chinese-speaking Telegram groups dedicated to hacking and penetration testing.
“In less than two months, we have identified yet another threat actor conducting SQL injection attacks against companies in the Asia-Pacific region,” says Nikita Rostovcev, senior analyst at the Advanced Persistent Threat Research Team, Group-IB.
“It is striking to see how some of the oldest yet remarkably effective SQL attacks remain prevalent in the region. However, the tenacity of the ResumeLooters group stands out as they experiment with diverse methods of exploiting vulnerabilities, including XSS attacks. Additionally, the gang’s attacks cover a vast geographical area.”
ResumeLooters have stolen databases that contain 2,079,027 unique emails and other records. (Source – Group-IB).
Other threats in the region
Apart from ResumeLooters, Group-IB also issued a report on GambleForce in December 2023. This cyberthreat group conducted over 20 SQL injection attacks against gambling and government websites in the region.
Unlike GambleForce, which focuses solely on SQL injections, ResumeLooters has a more diverse modus operandi. In addition to SQL injection attacks, they have successfully executed XSS scripts on at least four legitimate job search websites. On one of these websites, the attackers implanted a malicious script by creating a fake employer profile.
As a result, the attackers were able to steal the HTML code of the pages visited by the victims, including those with administrative access. Malicious XSS scripts were also intended to display phishing forms on legitimate resources. It is believed that the attackers’ main goal was to steal admin credentials. However, no evidence of successful theft of administrative credentials was found.
Protecting SQL databases
As SQL is used by almost all enterprises, businesses are recommended to use parameterized or prepared statements instead of directly concatenating user input into SQL queries to protect themselves against injection attacks.
Group-IB believes it is essential to implement comprehensive input validation and sanitization on both the client and server sides. The cybersecurity company also recommends businesses perform regular security assessments and code reviews helps to identify and mitigate injection vulnerabilities.
READ MORE
- 3 Steps to Successfully Automate Copilot for Microsoft 365 Implementation
- Trustworthy AI – the Promise of Enterprise-Friendly Generative Machine Learning with Dell and NVIDIA
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications




