
(Source – Shutterstock)
Organizations facing problems in zero-trust implementation
- A vast majority of Fortinet survey respondents reported that they already have a zero-trust and/or ZTNA strategy in place or development
- More than half of the respondents can’t authenticate users and devices on an ongoing basis and are struggling to monitor users’ post-authentication.
- More than 80% felt that implementing a zero-trust strategy across an extended network wasn’t going to be easy.
Over the last two years, zero-trust has been a buzzword in cybersecurity. Given the concerns that arose from remote working and speed businesses had to transform due to the pandemic, many organizations saw zero trust as the answer to have better visibility over who exactly is accessing their company data and workloads.
Most tech experts and C-level executives have voiced support for a zero-trust security model. In fact, Gartner reports that by 2022, 80% of new digital business applications will be accessed through zero-trust network access (ZTNA), with 60% of enterprises phasing out their remote access virtual private networks by 2023.
The concept of zero-trust is simple. It assumes anyone or anything that gains access to a network is not trusted. Nothing can be trusted anywhere, whether outside or inside the network perimeter.
Interestingly though, a new survey from Fortinet showed that although many organizations have a vision for zero-trust, that vision isn’t necessarily being translated into the solutions they’re able to put in place. Simply put, businesses are still granting trust, and granting too much trust can have dire consequences.
The bigger picture
The survey showed that organizations see the benefits of the zero-trust security model, with a vast majority of the survey respondents reporting that they already have a zero-trust and/or ZTNA strategy in place or development. And 40% report that their strategy is fully implemented.
At the same time though, more than half of the respondents don’t have the ability to authenticate users and devices on an ongoing basis and are struggling to monitor users’ post-authentication. These functions are critical tenets of the zero-trust philosophy, which makes one wonder what type of zero-trust implementation these organizations actually have.
It’s possible that although the survey respondents feel they have implemented zero trust, they may not truly have done so. Or perhaps, that they have incomplete deployments. Either way, the resulting lack of security is concerning.
80% of respondents also felt that implementing a zero-trust strategy across an extended network wasn’t going to be easy. Most of them (60%) report it would be moderately or very difficult, and another 21% said it would be extremely difficult.
(Source – Fortinet)
Survey respondents almost universally acknowledge that it is vital for zero-trust security solutions to be integrated with their infrastructure, work across cloud and on-premises environments, and be secure at the application layer.
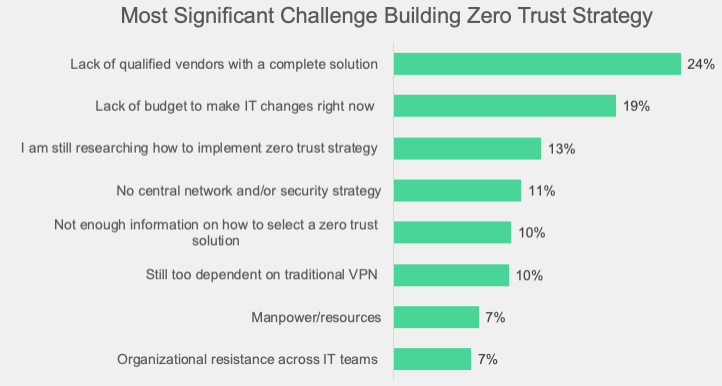
However, even realizing the importance of integration, the most prominent challenge organizations report facing in building a ZTNA strategy is the lack of qualified vendors with a complete solution.
Zero-trust needs to happen
With more organizations supporting remote work and work-from-anywhere initiatives, zero-trust is not likely to go away. The more people work from anywhere, the less secure a traditional perimeter-based approach becomes. Because the philosophy is about “securing work and learning everywhere,” it is a good way to secure hybrid working models and should be included as part of any comprehensive cybersecurity strategy.
An effective zero-trust solution requires elements designed to work together as an integrated system to prevent the types of security and management gaps that have challenged survey respondents.
A proper zero-trust solution is all about knowing exactly who and what is on the network at any given moment and that authenticated users and devices are only provided with the minimum level of access for them to do their job. So, when organizations report that they aren’t able to authenticate users and devices on an ongoing basis and struggle to monitor users for authentication, zero trust isn’t doing its job.
READ MORE
- 3 Steps to Successfully Automate Copilot for Microsoft 365 Implementation
- Trustworthy AI – the Promise of Enterprise-Friendly Generative Machine Learning with Dell and NVIDIA
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications


