
(Source – Shutterstock)
ZTNA 2.0 – Zero trust with zero exceptions
One of the biggest problems of zero trust network access (ZTNA) faced by companies is ensuring it can be implemented fully. Since the security framework was first introduced, zero trust has become one of the most practiced cybersecurity measures taken by companies.
In fact, according to a white paper by ESG, 59% of IT decision-makers said that cybersecurity has become more difficult over the last two years, with remote and hybrid work being one of the biggest reasons for it. They also felt that issues related to the changing threat landscape, the increase in the number of cloud applications used by their organizations, and the need to connect third-party users to corporate resources also made it harder to manage cybersecurity.
As such, organizations opted for ZTNA, which is predominantly the essential element of any approach to networking and security in the hybrid or remote working world. However, the white paper states that actual deployments are still taking time to catch on, with 54% of respondents to an ESG survey stating that their current organization’s zero trust initiative has been in place for less than two years.
So why is implementing zero trust a big challenge? According to the report, the primary issues with zero trust have to do with access controls, least-privilege access, a lack of visibility as well as an “allow and ignore” model that trusts but rarely verifies. As such, the full principles of zero trust are not being followed or enforced.
With that said, Palo Alto Networks has urged the industry to move to Zero Trust Network Access 2.0 or ZTNA 2.0, the foundation for a new era of secure access. As ZTNA was developed as a replacement for virtual private networks (VPNs) when it became clear that most VPNs did not adequately scale and were overly permissive, the first-generation ZTNA products were still too trusting, putting customers at significant risk. ZTNA 2.0 solves these problems by removing implicit trust to help ensure organizations are properly secured.
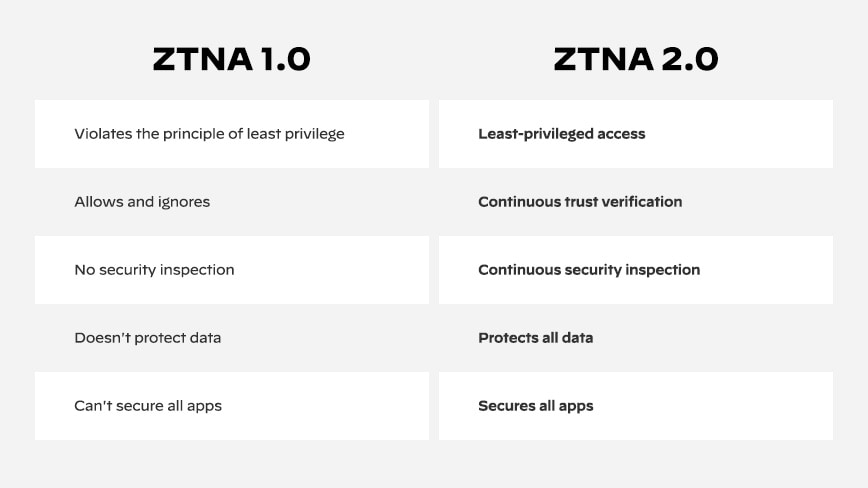
ZTNA 1.0 vs ZTNA 2.0
“This is a critical time for cybersecurity. We are in an era of unprecedented cyberattacks, and the past two years have dramatically changed work — for many, work is now an activity, not a place. This means that securing employees and the applications they need is both harder and more important,” said Nir Zuk, founder, and chief technology officer at Palo Alto Networks.
Zuk also pointed out that unfortunately, not every solution with zero trust in its name can be trusted which is why ZTNA 1.0 fell short.
For modern organizations where hybrid work and distributed applications are the new normal, ZTNA 1.0 has several limitations. As mentioned earlier, it is overly permissive in granting access to applications because it can’t control access to sub-applications or particular functions. Additionally, there is no monitoring of changes in user, application, or device behavior, and it can’t detect or prevent malware or lateral movement across connections. ZTNA 1.0 also cannot protect all enterprise data.
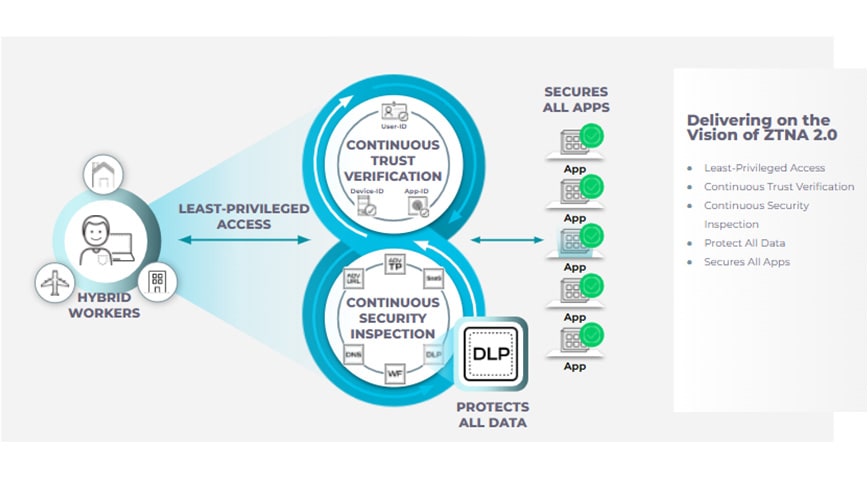
ZTNA 2.0
On the other hand, Zero trust 2.0-capable products help organizations meet the security challenges of modern applications, threats, and the hybrid workforce. ZTNA 2.0 incorporates the following key principles:
- Least-privileged access — enables precise access control at the application and sub-application levels, independent of network constructs like IP addresses and port numbers.
- Continuous trust verification — after access to an application is granted, continuous trust assessment is ongoing based on changes in device posture, user behavior, and application behavior.
- Continuous security inspection — uses deep and ongoing inspection of all application traffic, even for allowed connections to help prevent threats, including zero-day threats.
- Protection of all data — provides consistent control of data across all applications, including private applications and SaaS applications, with a single data loss prevention (DLP) policy.
- Security for all applications — consistently secures all types of applications used across the enterprise, including modern cloud-native applications, legacy private applications, and SaaS applications.
John Grady, ESG senior analyst who wrote the white paper, said, “first-generation/ZTNA 1.0 solutions fall short in many ways on delivering on the promise of true zero trust. In fact, they grant more access than is desired. What’s more, once access is granted in ZTNA 1.0 solutions, the connection is implicitly trusted forever, allowing a handy exploit route for sophisticated threats and/or malicious actions and behavior.”
For Grady, it is time to embrace a new approach to ZTNA, with zero trust 2.0 being one that has been designed from the ground up to meet the specific challenges of modern applications, threats, and a hybrid workforce.
READ MORE
- 3 Steps to Successfully Automate Copilot for Microsoft 365 Implementation
- Trustworthy AI – the Promise of Enterprise-Friendly Generative Machine Learning with Dell and NVIDIA
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications


