Chinese hackers suspected of being state-sponsored are theorized to have launched these attacks on SEA countries disputing parts of the South China Sea (IMG/Shutterstock)
State-sponsored Chinese hackers target Southeast Asian govts, militaries: report
Chinese hackers, likely state-sponsored, have been broadly targeting government and private-sector organizations across Southeast Asia.
These include those closely involved with Beijing on infrastructure development projects, according to a report released this Wednesday by Insikt Group.
The group, part of private Masachussets-based cybersecurity firm Recorded Future, tracked Chinese state-sponsored cyber-espionage operations targeting government and private sector organizations across Southeast Asia this year.
Hackers ‘likely linked’ to Chinese state government
According to Insikt, the identified intrusion campaigns “almost certainly support key strategic aims of the Chinese government”.
These include gathering intelligence on countries engaged in territorial disputes related to the South China Sea or related to projects and countries strategically important to the Belt and Road Initiative (BRI).
The report highlighted ‘Threat Activity Group 16’ (TAG-161 ), which has compromised several high-profile military and government organizations across Southeast Asia throughout 2021.
These attacks, claim the group, have utilized custom malware families such as FunnyDream and Chinoxy. Many of the governments targeted by TAG-16 are engaged in ongoing disputes with China over territorial claims in the South China Sea.
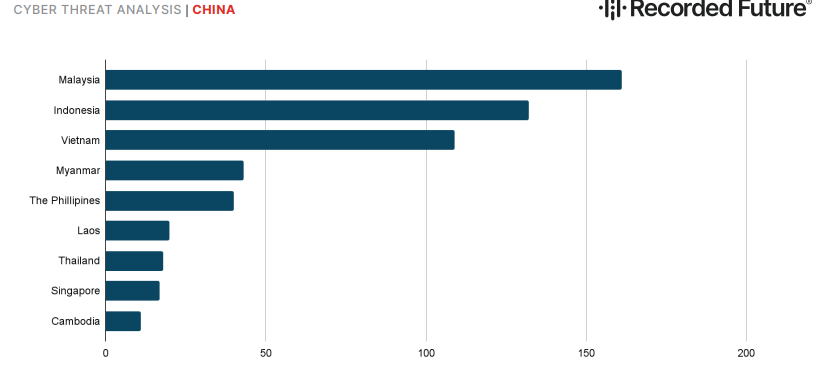
Suspected Chinese state-sponsored intrusions targeting Southeast Asia by country in the past 9 months. The number of victim organizations is likely smaller than the number of victim IPs listed due to IP reassignment and other technical considerations. (IMG/Recorded Future)
Using Recorded Future adversary infrastructure detection and Network Traffic Analysis (NTA) techniques, in the past 9 months, Insikt Group identified over 400 unique victim servers located in Southeast Asia.
The top 3 targeted countries within their data set were Malaysia, Indonesia, and Vietnam, with known groups active in the region including RedDelta, Naikon, and Goblin Panda, as well as temporary clusters grouped as TAG-16 and TAG-22.
The group had, in April 2021, reported that multiple government organizations across Vietnam, Malaysia, Indonesia, Thailand, and the Philippines were communicating with TAG-16 C2 infrastructure, and with likely links to Chinese state-sponsored actors.
Not the first instance of attacks
In November 2020, Bitdefender reported on a TAG-16 campaign targeting Southeast Asian government institutions using the Chinoxy, FunnyDream, and PCShare backdoors.
While the group behind this activity was unnamed, Kaspersky and PWC have also briefly referenced this FunnyDream campaign, with PWC tracking the group as Red Hariasa.
Notably, Insikt Group identified the compromise of navies, prime minister’s offices, ministries of defense, and ministries of foreign affairs across several countries with a presence in the South China Sea.
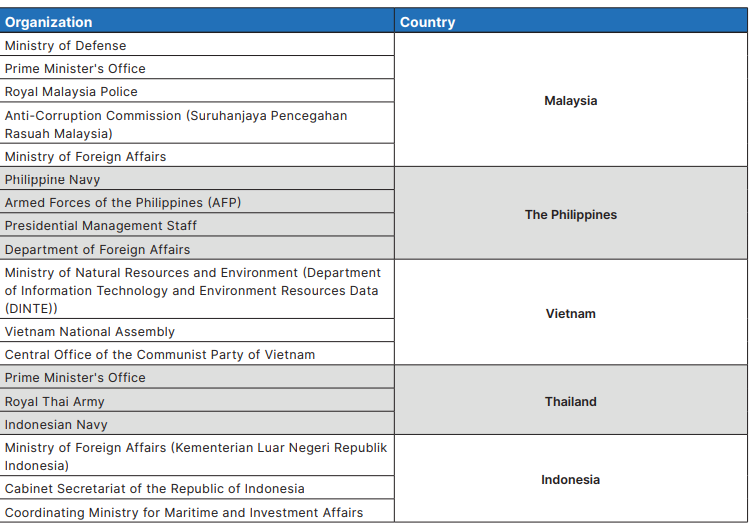
Sample of identified TAG-16 victims (IMG/ Recorded Future)
The targeting of Cambodia’s Sihanoukville Autonomous Port (PAS) and Laos’s National Committee for SEZs (special economic zones) are likely linked to China’s wider strategic objectives under the BRI.
PAS has high strategic significance given its location along the Maritime Silk Road route, while the Lao government has promoted the development of SEZs as an entry point for private sector development, including domestic and foreign direct investment (FDI).
“We believe this activity is highly likely to be a state actor as the observed long-term targeted intrusions into high-value government and political targets is consistent with cyber-espionage activity, coupled with identified technical links to known Chinese state-sponsored activity,” the company told The Associated Press.
In the past, Chinese authorities have consistently denied any form of state-sponsored hacking, instead, saying China itself is a major target of cyberattacks.
All countries affected were notified of these findings in October, although the firm said that some of these activities are still ongoing, reported Nikkei Asia.
Additionally, it was reported that Chinese hackers have also exploited the latest Log4j (or Log4Shell) vulnerabilities.
READ MORE
- 3 Steps to Successfully Automate Copilot for Microsoft 365 Implementation
- Trustworthy AI – the Promise of Enterprise-Friendly Generative Machine Learning with Dell and NVIDIA
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
