
Protect your Apple device: Immediate software update recommended (Source – Shutterstock)
Security alert: update your Apple software to avoid zero-click spyware
- Apple security alert: Newly discovered zero-click spyware targets iPhones and threatens national security.
- Update now to activate Apple’s Lockdown Mode and protect your device.
- The zero-click threat model is increasingly used to target particular groups of victims.
Apple security alert: in a rapidly evolving cybersecurity landscape, the safety of your personal data is more crucial than ever. A recent development has added a sense of urgency to this ongoing concern, specifically for users of Apple devices. Before delving into the details, we strongly advise all Apple users to take immediate action by updating their software.
The Apple security alert follows Canadian researchers’ discovery of a “zero-click” security flaw. This vulnerability lets hackers install spyware on iPhones without requiring any action from the users.
The Citizen Lab’s discovery and its implications on the new Apple security alert
The Citizen Lab, part of the University of Toronto’s Munk School, announced recently that this security gap is being exploited to compromise iPhones operating on iOS 16.6.
According to The Citizen Lab, cyberattackers are transmitting harmful images via widely used messaging apps like iMessage. Unusually, the devices can get infected even if users don’t engage with the malicious content.
Senior researcher John Scott-Railton from The Citizen Lab clarified that the flaw qualifies as a “zero-click” vulnerability because it needs no interaction from the victim for the device to be compromised.
He further emphasized the seriousness of this spyware, stating it could compromise national security and is particularly risky for individuals in professions that might make them a valuable target.
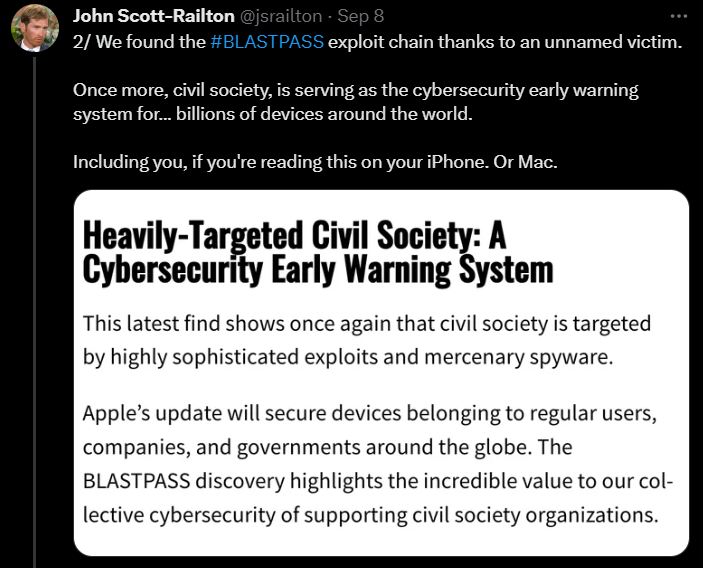
John Scott-Railton took to X to let users know about the new zero-click exploit chain. (Source – X)
It’s not the first instance of zero-click vulnerabilities affecting Apple devices. Moscow’s cybersecurity firm, Kaspersky, has noted that an unidentified malware is currently targeting iOS devices.
Dubbed Operation Triangulation, Kaspersky’s report outlines the attack mechanics and its technical specifics. The report also suggests that the earliest signs of such attacks trace back to 2019, and are still taking place, affecting up to iOS version 15.7.
Kaspersky’s findings have stirred up controversy, as Russia’s Federal Security Service accuses the malware of targeting thousands, including foreign officials. They’ve implicated Apple and the U.S. National Security Agency in orchestrating these attacks, a claim Apple has refuted.
How zero-click spyware attacks operate
This newly identified iOS flaw operates through a zero-click mechanism, distinguishing it from common malware attacks that require user action.
Kaspersky conducted a timeline analysis of compromised devices to understand the infection process. The attack is initiated when a malicious message arrives on the targeted iPhone via iMessage. This message carries an attachment containing the exploit. As soon as the message lands on the device, the vulnerability is triggered, executing malicious code.
Subsequent stages of the attack involve the download of additional exploits from a Command and Control (C&C) server, controlled by the attacker, to escalate privileges. Once the exploit succeeds, a final payload is retrieved from the C&C server, after which the original message and attachment are deleted. Kaspersky noted that the malware lacks persistence capabilities, most likely due to operating system limitations. Yet, repeated infections are possible upon device reboot.
The company also added that the final analysis of the malware payload is pending, but preliminary findings indicate that it runs on root privileges and can collect an array of system and user data.
Senior researcher Scott-Railton warned that the risk is particularly high for individuals in legal, journalistic, and financial sectors, noting that users can’t easily detect such an infection.
Apple security alert: Steps to enhance your device’s security
Upon learning of the vulnerability, The Citizen Lab promptly alerted Apple, releasing an immediate security patch. Apple accompanied the update with a statement acknowledging the ongoing exploitation of this security loophole. To bolster device safety, The Citizen Lab advises activating Lockdown Mode, in addition to updating to the latest security patch.
Apple’s Lockdown Mode enhances device protection by restricting certain app functionalities and features. For instance, most attachments and links won’t display in messages when this mode is on.
To activate Lockdown Mode, go to Settings > Privacy & Security > Tap on “Lockdown Mode” > Enable. A device restart is needed to activate this function.
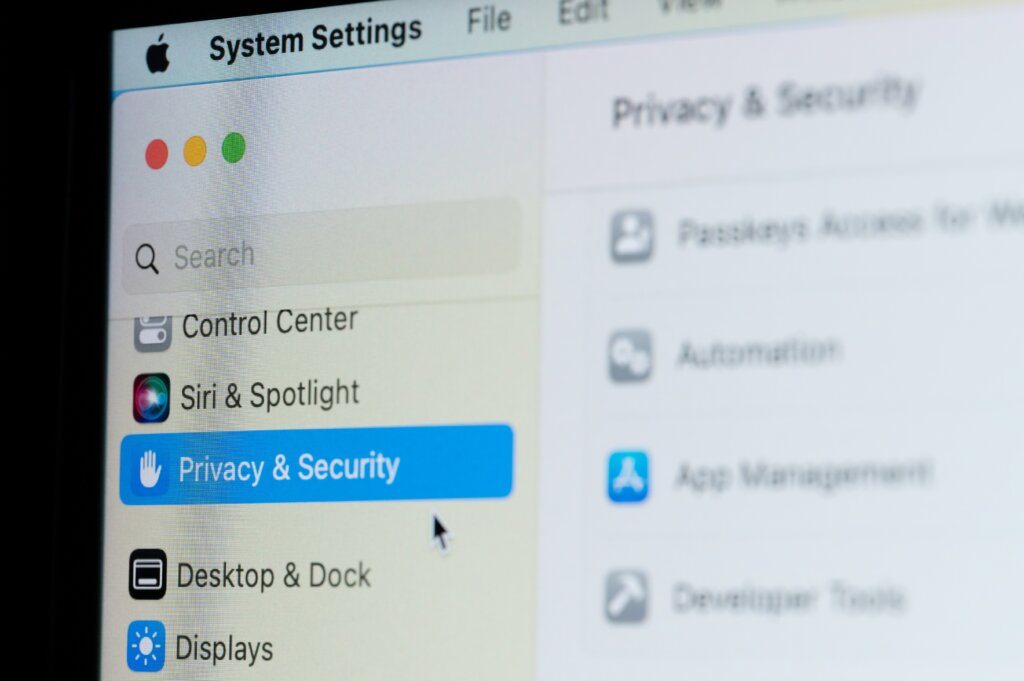
Steps to enhance your device’s security with the new Apple security alert. (Source – Shutterstock)
According to another senior researcher at The Citizen Lab, Bill Marczak, Lockdown Mode has proven effective against the Pegasus spyware, which was seen in recent compromises. “NSO Group despises the Lockdown Mode. If you’re at risk, activate it and stay secure,” Marczak stated.
International impact and policy responses
Controversial for their spyware technologies, the NSO Group and similar firms have been scrutinized extensively. In March, Canada, alongside the U.S., Australia, Costa Rica, Denmark, France, New Zealand, Norway, Sweden, Switzerland and the United Kingdom, declared a cooperative effort to limit the usage of harmful spyware against political opponents, journalists, and human rights activists.
A joint statement from these nations expressed their collective aim to formulate policies that discourage commercial spyware abuse. Scott-Railton suggested that such technology has likely compromised thousands of individuals, usually without their being aware.
Previously, in 2019, over 1,400 phones were attacked through WhatsApp by NSO Group-related zero-click spyware.
The following year, 36 personal phones of staff at Al Jazeera, including journalists and executives, were compromised by governmental entities utilizing NSO Group’s Pegasus spyware.
The recent Apple security alert serves as a sobering reminder of the evolving nature of threats in our digital age. While tech companies like Apple are continuously working to patch vulnerabilities, the onus is increasingly on users to be vigilant about their own cybersecurity. Stay informed, stay updated, and, most importantly, stay secure.
READ MORE
- 3 Steps to Successfully Automate Copilot for Microsoft 365 Implementation
- Trustworthy AI – the Promise of Enterprise-Friendly Generative Machine Learning with Dell and NVIDIA
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications






